
|
|
Biometrics on NGSCB |
An NGSCB system consists of two largely isolated operating environments that share hardware resources, including the CPU, RAM, and some I/O devices. In the following figure, the vertical line between the two operating environments represents a hardware- and software-based isolation mechanism. The environment to the left of the vertical line (standard mode) is the traditional operating system with some special support for NGSCB. The environment to the right of the vertical line (nexus mode) is a protected operating environment in “curtained memory” (an area of memory that is isolated from the rest of the system), which contains two primary components:
· Nexus: A special security kernel that establishes the protected operating environment by isolating specific areas in memory. The nexus provides encryption technology to authenticate and protect data that is entered, stored, communicated, or displayed on the computer and to help ensure that the data is not accessed by other applications and hardware devices.
· Nexus computing agent (NCA): A trusted software component, hosted by the nexus, that runs in the protected operating environment. An NCA can be an application, a part of an application, or a service. Using an NCA to process data and transactions in a protected operating environment is one of the primary features used to enhance security on NGSCB-capable computers.
NGSCB-enabled devices for two-factor authentication, a smart card reader and biometric input device, are attached to the system depicted in the figure, while the user authentication software component runs as an NCA in the protected operating environment.
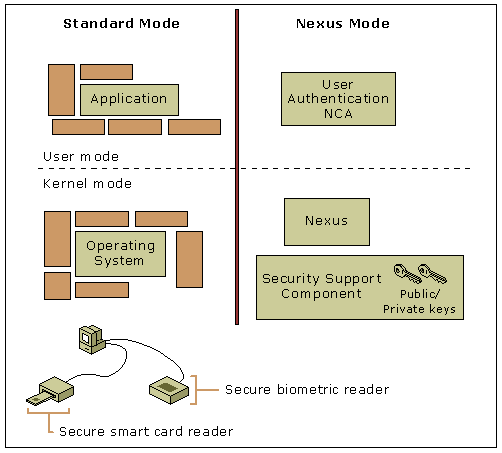
An NGSCB system configured for two-factor authentication
If the system administrator does not choose to "opt-in" and turn on NGSCB, users are authenticated in the standard way: using information provided by the smart card and biometric device (two-factor authentication). If the system administrator "opts-in" and turns on NGSCB, and if the authentication input devices are NGSCB-enabled, a path for secure input is set up between the devices and the NGSCB-enabled application (in this case, the user authentication NCA). NGSCB adds the following secure input capabilities to two-factor authentication to provide the strongest possible user authentication:
· Integrity: The NGSCB system verifies that user authentication information was not modified after it was submitted. For example, the system verifies that another entity did not substitute different information.
· Confidentiality: The NGSCB system maintains the security of the user authentication information by ensuring that no other entity can read the information.
· Authentication: The NGSCB system verifies that the user authentication information it receives is submitted by secure input devices. No other entity could have sent the information.
The secure input mechanism helps to protect the computer against programs that can read keystrokes or allow a remote user or program to act as a legitimate local user. NGSCB supports secure input through upgraded keyboards and Universal Serial Bus (USB) devices, allowing a local user at a local keyboard or other device to communicate privately with an NCA. Smart cards, biometrics, and other authentication input devices are made trustworthy by embedding an input security support component (ISSC) into the device or into the hub to which the device connects. When these devices are plugged into the computer, and the NGSCB system is turned on, the system can determine whether the devices are secure and set up a path for the exchange of authentication information between the devices and the user authentication software component NCA that is running in the computer's protected operating environment.